
Components of Surveillance Solution
CCTV (Closed Circuit Television), is a system that allows you to keep an eye on what’s going on in and around your business. Cameras and monitors enable you to view events live, VMS helps you record the cameras and recorders archive footage for later reference. Don’t mistake a CCTV monitor for an ordinary television. It doesn’t receive publicly broadcasted content—only footage from security cameras installed on the premises.
CCTV technology has been around for decades, but improvements in recent years make it even more effective at capturing criminals in the act and bringing them to justice. Consider the various parts of a CCTV system and how they all work together.
Do you want to improve the security of your business / home / any other location? Bangalore Datacom specializes in the design, installation, and maintenance of custom CCTV video surveillance systems for you.Our video surveillance installation team can perform a site evaluation in order to determine the type, placement, and a number of surveillance cameras necessary to meet your needs.

Next, we’ll set up a video surveillance camera system from Axis Communications that’s easy to operate along with Milestone Systems Video Management Software helps to record Axis cameras, can guarantee you peace of mind. We can be your trusted advisor and also recommend you the solution depending on your needs. Leave the rest and enjoy the best.
Contact us to schedule an on-site survey and estimate for a video surveillance system installation or maintenance from Bangalore Datacom. No matter what your security and surveillance needs are, our team have the experience and expertise to find the best solution as per your requirements.

Camera
A network camera, often also called an IP camera, can be described as a camera and computer combined in one unit. The main components of a network camera include a lens, an image sensor, one or several processors, and memory. The processors are used for image processing, compression, video analysis and networking functionalities. The memory is used for storing the network camera’s firmware (computer program) and for local recording of video sequences.
Like a computer, the network camera has its own IP address, is connected directly to a network and can be placed wherever there is a network connection. This differs from a web camera, which can only operate when it is connected to a personal computer (PC) via the USB or IEEE 1394 port, and to use it, software must be installed on the PC. A network camera provides web server, FTP (File Transfer Protocol), and e-mail functionalities, and includes many other IP network and security protocols.

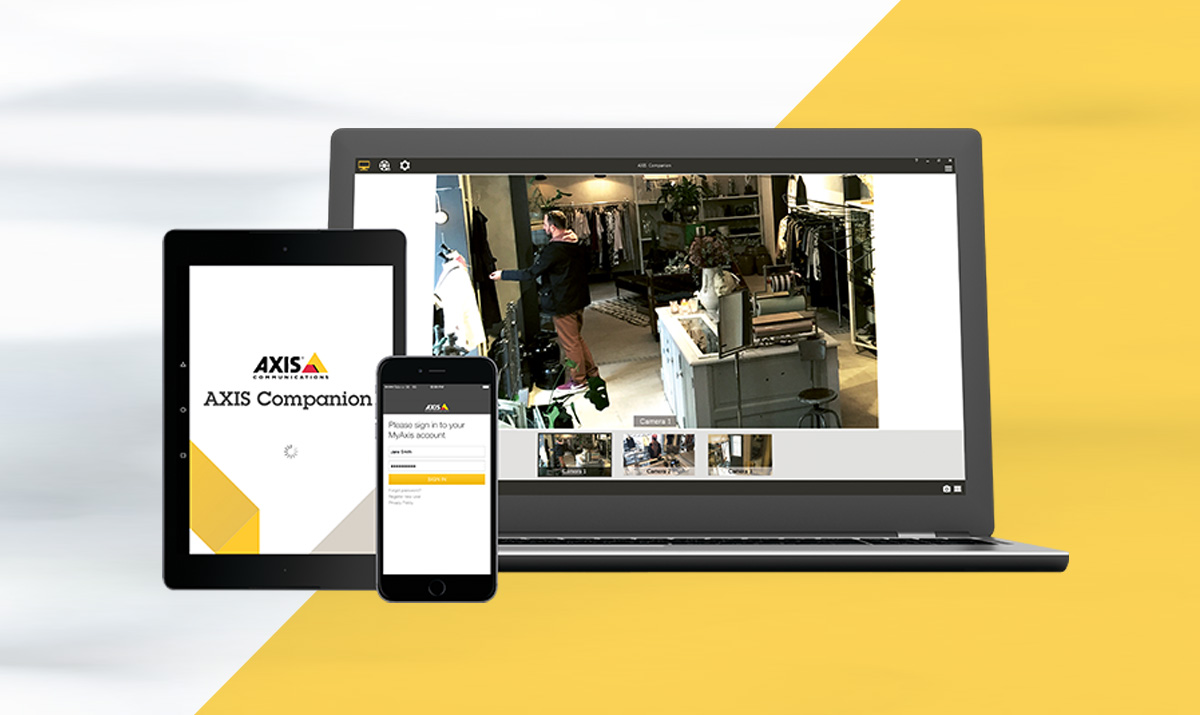
VMS
The core of your security solution is the Video Management Software (VMS). Deciding software for your solution is not only a matter of size. Even more important is what security issues you have and how they can be best addressed.
Video Management Softwares are designed and validated to perfectly record the cameras and features. The solutions can be easily adapted to your business, and seamlessly expand with your needs. Because when your business grows, so should your security solution.
A video management system, also known as video management software or a video management server, is a component of a security camera system that in general:
- Collects video from cameras and other sources
- Records / stores that video to a storage device
- Provides an interface to both view the live video, and access recorded video
A VMS can be the software component of a network video recorder and digital video recorder, though in general a VMS tends to be more sophisticated and provide more options and capabilities than a packaged NVR device.
Due to improvements in technology, it is necessary to make a distinction between a VMS and the built-in features of modern network based security cameras. Many modern network cameras offer internal capabilities to record and review video directly themselves via a web browser and without the use of a VMS. However a camera's built-in web interface is typically exclusive to the camera itself and does not normally provide a shared access capability across other network cameras.

Audio Solutions
Many video surveillance cameras support a microphone (in-built, with the option for an external unit) and support external speakers. Audio adds value to surveillance content, in specific cases and provided it is of a quality that can be comprehended.
How effective are the audio components of a video surveillance camera, and what are the use-cases for deploying the audio-input and audio-output features of a video surveillance camera. This brief looks at the standards, the effectiveness, and use-cases with respect to the audio components of a video surveillance solution.
Audio solutions can be used for numerous applications; enhancing video surveillance as a deterrent to crime, helping deal with incidents ahead of arrival by first responders, providing guidance and instruction, and effectively adding another ‘sense’ to surveillance.
As a deterrent to potential crime, vandalism and anti-social behaviour, live and pre-recorded audio announcements are more effective and efficient than standard sirens. Live call outs are highly effective in monitored surveillance systems, where operators can give detailed instruction based on the specific situation, or issue warnings.
When video surveillance operators identify an individual committing or looking likely to commit a crime, the ability to issue a warning to that specific individual is highly effective. “To the young man in the blue jacket and baseball cap, holding a can of spray paint, be aware that you are on camera and that graffiti is vandalism and illegal…” is likely to stop them in their tracks.

Security Radar
The strongest security solutions take advantage of a strategic mix of technologies to achieve the best results. Every tool in the toolbox has a role to play, and radar’s is an important one.
Radar keeps false alarms to a minimum. And it provides crucial information about detected objects that video cameras can’t – such as their exact position, and the speed and direction of their movement.
It is perfect for wide-open, outdoor areas with moderate activity. For example fenced-off area for stock or industrial sites or even to detect façade climbers and to prevent intrusion from the roof.
Radar is an established detection technology based on radio waves. It is increasingly used in consumer products because modern radar devices can be small and chip based. Being based on a non-visual technology, radar has a lot to offer in surveillance. Security radar works well in many situations where other surveillance technologies may fail, such as in poor lighting, darkness, and fog. Radar is also stable in many situations where video surveillance with analytics software are likely to create false alarms, for example, when there are moving shadows or lights in the scene, in bad weather, or when there are raindrops or insects on the device. Radar also has the benefit of providing surveillance that maintains privacy because people can’t be identified from the radar information. Security radar from Axis can be used on its own, for example in environments where cameras aren’t allowed due to privacy concerns. But radar is primarily integrated into a security system with video and audio products. Just like Axis cameras, Axis security radars are compatible with major video management systems (VMS) and can be set up to trigger a range of actions upon detection. With Axis radar, no additional analytics applications are needed, since detection, tracking, and classification of objects are all integrated in the radar device. A deep learning classifier algorithm distinguishes the type of detected object, for example a human or a vehicle. Axis has used both machine learning and deep learning to develop the algorithm. Radar devices are commonly combined with visual cameras for identification of individuals. This is especially effective with PTZ (pan-tilt-zoom) cameras, which can track and identify persons or vehicles based on their exact geographical position provided by the radar. Radars are also often used together with thermal cameras, where the radar devices’ wide area detection combines well with thermal cameras’ narrow but long detection area. Radar and audio are also a good combination where visual identification either isn’t allowed or isn’t prioritized. A deterring audio message may very well stop an intruder detected by the radar
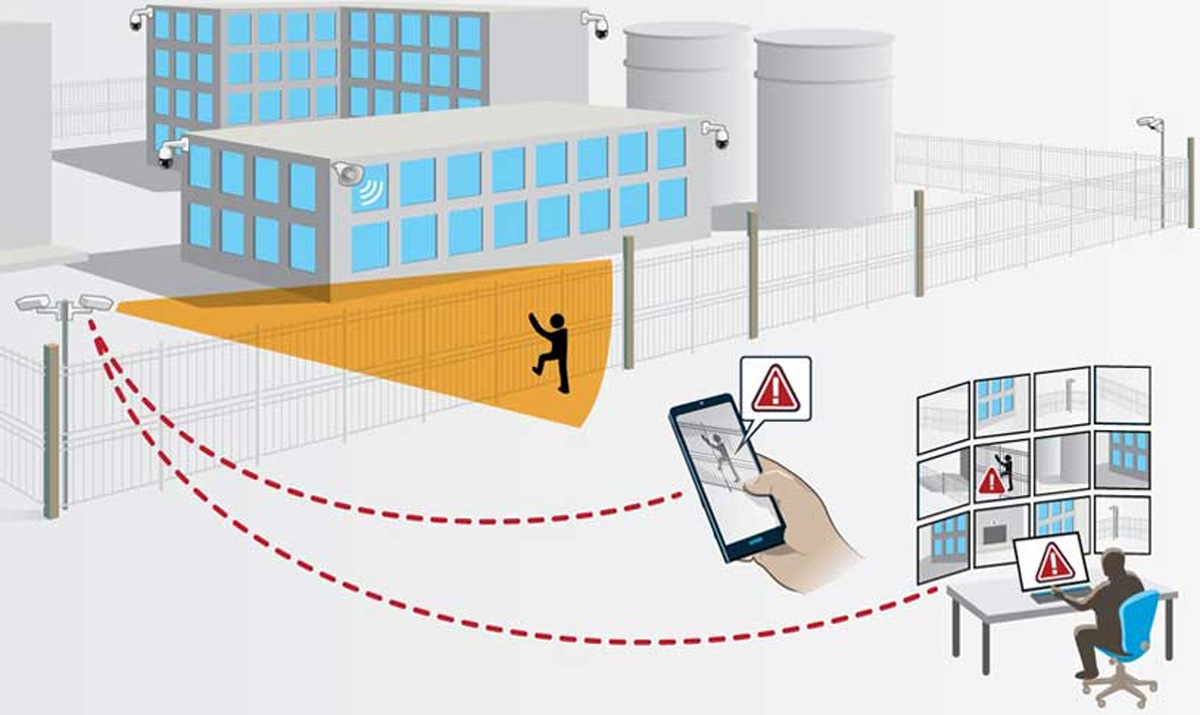
Video Analytics
Analytics is the systematic computational analysis of data or statistics. It is used for the discovery, interpretation, and communication of meaningful patterns in data. It also entails applying data patterns towards effective decision making. It can be valuable in areas rich with recorded information; analytics relies on the simultaneous application of statistics, computer programming and operations research to quantify performance. Organizations may apply analytics to business data to describe, predict, and improve business performance.
Video analytics or intelligent video surveillance (IVS) is a technology that uses software to automatically identify specific objects, behaviour or attitudes in video footage. It is basically used for intrusion detection. It transfers to the software the human interventions normally required to detect intrusions. It has the capability to analyse a video frame or a group of video frames to detect, classify, recognise or identify a predetermined event that has been programmed through the IVS software. It uses mathematical algorithms to detect moving objects in an image and filter non-relevant movements. It then creates a database that records the attributes of all the objects detected and their movement.
“Each surveillance camera automatically identifies activities and objects during continuous real-time image analysis, and alerts the operator by sending an alarm when it detects a critical event,” informs Ajay Sahney, senior general manager and country head, Bosch Security Systems.
In short, video analytics technology will enable users to manage a vast mass of undifferentiated data that they may receive from different cameras and turn it into useful information. This will turn their cameras into predictive tools that will allow them to spot problems brewing and prevent incidents in a more proactive manner, rather than just filming the events for later investigative use.
“Video analytics uses a variety of rules, which can be specifically customised both for the scene and the objects being observed, in order to intelligently identify potentially suspicious behaviour.”
By using multiple customised rules and algorithms that will screen out adverse weather, the effects of changing light conditions, and non-critical movement, analytics systems let security staff focus on real incidents rather than getting bogged down with hundreds of false alarms. This technology also requires less time to monitor multiple video feeds within your CCTV system and allows quicker responses.
“No matter how many cameras a system uses, monitoring everything effectively is a serious challenge. Even by observing one camera for long, an operator can miss out on important activities. Bosch intelligent video analysis (IVA) helps operators to stay focused by introducing a new level of automation to CCTV monitoring. Edge-based, real-time processing identifies alert conditions, giving your security team the information it needs to react swiftly and take action.”
We can help you with analytics like COVID-19, Face Recognition, Counting, Flow, Parking, Traffic, trigger based, Business intelligence and many more.

Recorder
A network video recorder (NVR) is a specialized computer system that includes a software program that records video in a digital format to a disk drive, USB flash drive, SD memory card or other mass storage device. An NVR contains no dedicated video capture hardware. However, the software is typically run on a dedicated device, usually with an embedded operating system. Alternatively, to help support increased functionality and serviceability, standard operating systems are used with standard processors and video management software. An NVR is typically deployed in an IP video surveillance system.
Network video recorders are distinct from digital video recorders (DVR) as their input is from a network rather than a direct connection to a video capture card or tuner. Video on a DVR is encoded and processed at the DVR, while video on an NVR is encoded and processed at the camera, then streamed to the NVR for storage or remote viewing. Additional processing may be done at the NVR, such as further compression or tagging with meta data.
Hybrid NVR/DVR surveillance systems exist which incorporate functions of both NVR and DVR; these are considered a form of NVR.
It can also be an attached storage or a server /computer system with video management software loaded in it, where the recordings can be stored for number of days desired.

Power
Most IP cameras work on PoE. So there is no need to put a separate power cable. The other end of patch cord goes to switch. Switch requires uninterrupted power. If there is a power failure to the switch the entire system will go down. Power surge also might damage the equipments.
When there is a power surge, the UPS helps prevent the devices being affected and damaged by it.
An uninterruptible power supply or uninterruptible power source (UPS) is an electrical apparatus that provides emergency power to a load when the input power source or mains power fails. A UPS differs from an auxiliary or emergency power system or standby generator in that it will provide near-instantaneous protection from input power interruptions, by supplying energy stored in batteries, super capacitors, or flywheels. The on-battery run-time of most uninterruptible power sources is relatively short (only a few minutes) but sufficient to start a standby power source or properly shut down the protected equipment. It is a type of continual power system.
A UPS is typically used to protect hardware such as computers, datacenters, telecommunication equipment or other electrical equipment where an unexpected power disruption could cause injuries, fatalities, serious business disruption or data loss.
The primary role of any UPS is to provide short-term power when the input power source fails. However, most UPS units are also capable in varying degrees of correcting common utility power problems:
- Voltage spike or sustained overvoltage
- Momentary or sustained reduction in input voltage
- Voltage sag
- Noise, defined as a high frequency transient or oscillation, usually injected into the line by nearby equipment
- Instability of the mains frequency
- Harmonic distortion, defined as a departure from the ideal sinusoidal waveform expected on the line

Switching
Switches are key building blocks for any network. They connect multiple devices, such as computers, wireless access points, printers, and servers; on the same network within a building or campus. A switch enables connected devices to share information and talk to each other.
Unmanaged switches
An unmanaged network switch is designed so that you can simply plug them in and they work, no configuration required. Unmanaged switches are typically for basic connectivity. You'll often see them used in home networks or wherever a few more ports are needed, such as at your desk, in a lab, or in a conference room.
Managed switches
Managed switches give you greater security and more features and flexibility because you can configure them to custom-fit your network. With this greater control, you can better protect your network and improve the quality of service for those who access the network.
How a Cisco Switch functions on an Ethernet network
Many of us use switches every day but never really think about how they work. Whether you are studying to become a CCNA or just want to learn more about how a switch really functions, this article is for you.
Hubs vs. Switches
Prior to switches, Hubs were the standard for connecting devices on a local area network (LAN). The problem with hubs was that everything that went through them had to share the bandwidth of the link, bandwidth was wasted because all traffic was sent to all devices, and there were a lot of collisions because the hub didn’t do anything to prevent them. A switch fixes these problems.
What do switches do?
Here are some facts about switches that you should know:
- Switches work at Layer 2 of the OSI model, not Layer 1 like a hub
- Switches switch Ethernet frames
- Switches don’t look at IP address information, only Ethernet MAC addresses
- Switches keeps a table of all MAC addresses traversing the switch and what port they are on (this table is called the bridge forwarding table or CAM table)
- Switches only sends traffic to the devices that are the destination for that traffic, saving bandwidth
- Each device connected to the switch gets the full bandwidth of the switch port because the switch prevents collisions
Flooding
Now that you know that the switch has the bridge forwarding table and uses that to intelligently send traffic, a common question is, “what if the destination MAC address for the traffic that the switch receives is not in the bridge forwarding table?” What does the switch do with that Ethernet frame? The answer is that the switch will flood that frame out all ports on the switch. The switch will then monitor the traffic for the response from that frame and see what device, on what port, responded to that flooded frame. That information will be put in the bridge forwarding table so that, next time, the switch won’t have to flood that traffic.
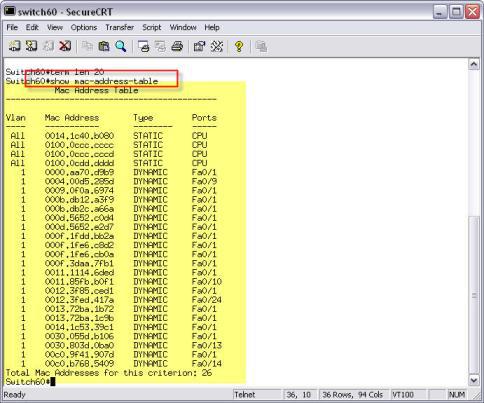
Bridge forwarding table
To see the bridge forwarding table on a Cisco switch, just type show mac-address-table, like this:
Port speed & Duplex
Of particular importance when it comes to switches are port speed and duplex. The speed of a port can be set to 10Mb, 100Mb, or 1000Mb (1GB), or Auto negotiate, depending on what the switch and the connecting device offers. Most switch ports and devices use auto negotiate to find the best speed and duplex available. However, this doesn’t always work. Some devices have trouble with this and you may have to go in to the switch and hardcode the speed or duplex.
Speaking of duplex, what is duplex? Duplex is set to either half, full, or is auto negotiated. A half duplex connection is where only one device can send or receive at a time. A full duplex connection is where both devices can send and receive at the same time.
Thus, if you have a 100Mb half-duplex connection, only sending at 100Mb OR receiving at 100Mb can happen at the same time. If you have a 100Mb full duplex connection, you can effectively get 200Mb out of the link because you could be sending 100Mb and receiving 100Mb at the same time.
Here is how you see the current speed and duplex of a switch port using the show interface command:
Most administrators will hard-code the port speed and duplex of servers to prevent auto negotiation. You don’t want your switch to reboot one night and, in the morning, have the email server connecting to the network at 10Mb half-duplex. You want the email server to either run at 1GB full duplex (for example) or not work at all.
Types of Switches
There are a number of different types of switches. You can buy a “dumb” switch for about $10 these days. It has no manageability and probably only 4-8 ports. From there, you can go up to an unmanaged 24 or 48 port switch.
However, most business users prefer a managed switch so that you can get statistics on switch traffic, see your bridge forwarding table, troubleshoot connections, and hard-code port speeds and duplex.
There are many brands of managed switches including, of course, Cisco. These managed switches come in sizes from just a few ports, all the way up to over 96 ports. You can even buy chassis-based switches, costing tens of thousands of dollars, like a Cisco Catalyst 6500 series switch. The chassis-based switches can have blades (cards) that perform not just switching but also routing, intrusion detection, and other services.
Another type of switch is called a Layer 3 switch. A Layer 3 switch is a switch that also has the routing functionality of a router but no WAN ports. Layer 3 switches are used primarily when a large company wants to use VLAN’s to segregate their network into logical networks.
Summary
Here is what we have learned:
- Switches work at Layer 2 of the OSI model, data-link
- Switches switch Ethernet frames
- Flooding is when a switch doesn’t have a destination MAC in its bridge forwarding table and it has to send that frame out to all ports
- Port speed and duplex are critical settings when it comes to connecting devices.
- There are many types of switches, managed, unmanaged, chassis-based, and layer 3.
Cabling
Technology is constantly evolving and changing, sometimes faster than you could ever guess. These new tools can make businesses more productive, secure and agile. However, these tools need the right network to support them.
Structured cabling is an infrastructure that’s made up of smaller, standardized elements. You can install structured cabling systems in a building or across a campus. It’s this kind of network cabling that can support all of the rapidly-advancing technology coming to the workplace.
Since the advent of personal computers, the introduction of laptops and VoIP calling systems, the demand on a business’s cable network has only grown. In the past, point-to-point cabling was used, which meant every piece of hardware used its own cable. The cabling literally ran from point to point. This would lead to a jumbled mess of wiring and cables that could be accidentally unplugged or present a safety hazard for tripping. To accommodate the rising need for speed and more bandwidth, structured cabling systems came into use and are now the best solution for a business’s network.
Structured cabling systems are a kind of network cabling solution that organizes your infrastructure. The beauty of structured cabling is that it helps to future-proof your business by accommodating any new hardware you add while supporting the increasing amount of data businesses use every day. It makes things much easier to manage as your business grows!
Structured cabling is the design and installation of a cabling system that will support multiple hardware uses and be suitable for today's needs and those of the future. With a correctly installed system, current and future requirements can be met, and hardware that is added in the future will be supported
Structured cabling design and installation is governed by a set of standards that specify wiring data centers, offices, and apartment buildings for data or voice communications using various kinds of cable, most commonly category 5e (Cat 5e), category 6 (Cat 6), and fiber optic cabling and modular connectors. These standards define how to lay the cabling in various topologies in order to meet the needs of the customer, typically using a central patch panel (which is normally 19-inch rack-mounted), from where each modular connection can be used as needed. Each outlet is then patched into a network switch (normally also rack-mounted) for network use or into an IP or PBX (private branch exchange) telephone system patch panel.
Lines patched as data ports into a network switch require simple straight-through patch cables at each end to connect a computer. Voice patches to PBXs in most countries require an adapter at the remote end to translate the configuration on 8P8C modular connectors into the local standard telephone wall socket. No adapter is needed in North America as the 6P2C and 6P4C plugs most commonly used with RJ11 and RJ14 telephone connections are physically and electrically compatible with the larger 8P8C socket. RJ25 and RJ61 connections are physically but not electrically compatible, and cannot be used.
- It is common to color-code patch panel cables to identify the type of connection, though structured cabling standards do not require it except in the demarcation wall field.
- Cabling standards require that all eight conductors in Cat 5e/6/6A cable be connected.
- IP phone systems can run the telephone and the computer on the same wires, eliminating the need for separate phone wiring.
- Regardless of copper cable type (Cat 5e/6/6A), the maximum distance is 90 m for the permanent link installation, plus an allowance for a combined 10 m of patch cords at the ends.
- Cat 5e and Cat 6 can both effectively run power over Ethernet (PoE) applications up to 90 m. However, due to greater power dissipation in Cat 5e cable, performance and power efficiency are higher when Cat 6A cabling is used to power and connect to PoE devices.
Subsystems
Structured cabling consists of six subsystems:
- Entrance facilities is the point where the telephone company network ends and connects with the on-premises wiring belonging to the customer.
- Equipment rooms house equipment and wiring consolidation points that serve the users inside the building or campus.
- Backbone cabling is the inter-building and intra-building cable connections in structured cabling between entrance facilities, equipment rooms and telecommunications closets. Backbone cabling consists of the transmission media, main and intermediate cross-connects and terminations at these locations. This system is mostly used in data centers.
- Horizontal cabling wiring can be standard inside wiring (IW) or plenum cabling and connects telecommunications rooms to individual outlets or work areas on the floor, usually through the wireways, conduits or ceiling spaces of each floor. A horizontal cross-connect is where the horizontal cabling connects to a patch panel or punch up block, which is connected by backbone cabling to the main distribution facility.
- Telecommunications rooms or telecommunications enclosure connects between the backbone cabling and horizontal cabling.
- Work-area components connect end-user equipment to outlets of the horizontal cabling system.
Standards
Network cabling standards are used internationally and are published by ISO/IEC, CENELEC and the Telecommunications Industry Association (TIA). Most European countries use CENELEC, International Electrotechnical Commission (IEC) or International Organization for Standardization (ISO) standards. The main CENELEC document is EN50173, which introduces contextual links to the full suite of CENELEC documents. ISO/IEC 11801 heads the ISO/IEC documentation. In the US, the Telecommunications Industry Association issue the TIA/EIA-568 standards for telecommunications cabling in commercial premises.
We are here to help
Speak to our team of experts today







